Orca Security found a critical design flaw in a Google Cloud Build that lets attackers escalate privileges for nearly full and unauthorized access to Google Artifact Registry code repositories.
The build flaw could allow hackers to impersonate the service account for the Google Cloud Build managed continuous integration and delivery (CI/CD) service to run API calls against the artifact registry, taking control of application images.
After deploying malicious applications into customers ‘ environments, the bad actors can then inject malicious code causing vulnerable applications and potential supply chain attacks.
The same vulnerability was observed and reported by Rhino Security Lab. However, the method to exploit the flaw was more complex. It involved using GCP API and exfiltrated Cloud Build Service Account access tokens.
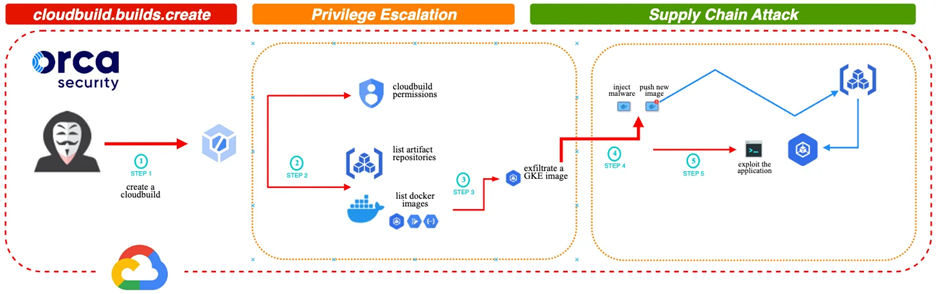
Orca Security’s attack takes advantage of the cloudbuild.builds.create permission and allow attackers to tamper with Google Kubernetes Engine (GKE) docker images using artifact registry permissions and run code inside the docker container as root.
Once notified, the Google Security Team implemented a partial fix revoking the logging.privateLogEntries.list permission from the default Cloud Build Service Account, unrelated to Artifact Registry. This did not directly address the underlying vulnerability in the Artifact Registry, leaving the privilege escalation vector and the risk of a supply chain attack intact. Customers are advised to modify the default Cloud Build Service Account permissions to match their needs, removing entitlement credentials that go against the Principle of Least Privilege (PoLP) to mitigate the privilege escalation risks.

