The UK and Republic of Korea (ROK) national cybersecurity organizations issued a joint warning of an increased volume and sophistication of North Korean software supply chain attacks.
South Korea’s National Intelligence Service (NIS) and the UK’s National Cyber Security Centre (NCSC) said Zero-day and N-day vulnerabilities are being used alongside multiple exploits to achieve goals that align closely with the “priorities” of North Korea. This includes generating funds, espionage, and the theft of IP and advanced technologies from industries including defense.
The advisory is the first published by the NCSC jointly with another cybersecurity agency without the input of any of its equivalents from the Five Eyes intelligence alliance. NCSC and NIS listed examples of zero-days and high-profile organizations exploited in attacks attributed to Lazarus, believed to be North Korea’s state-sponsored offensive cyber unit.
In March 2023, Lazarus attackers launched a watering hole attack on groups with vulnerable versions of the MagicLine4NX security authentication software installed. Initially, it compromised a media organization, poisoning a web page with malicious scripts so that when visited by a user with a vulnerable MagicLine4NX installed, it would execute and provide attackers with remote control capabilities on the victim’s machine via C2 infrastructure. A zero-day vulnerability was then exploited on a network-linked system via the compromised PC to breach a victim organization’s intranet to steal that organization’s data.
Security policies blocked the attackers, preventing a large-scale data theft incident. Despite not achieving the success North Korea would have wanted, the incident still provides evidence of Kim Jong Un’s ambition to target software supply chains with sophisticated methods.
The more widely publicized supply chain attack from North Korea this year is 3CX’s desktop app, one which was attributed to Lazarus. It affected high-profile targets, including two infrastructure organizations and financial trading companies. The attack impacted both Windows and macOS versions of the 3CX application. Lazarus breached the company and injected malicious code into its installer, which users downloaded through legitimate channels.
The infection chain was similar in both the Windows and Mac versions. Both applications installed normally, but once installed, the code entered a sleep phase – seven days for Windows and between seven and 20 days on Mac – before transmitting data to the attackers.
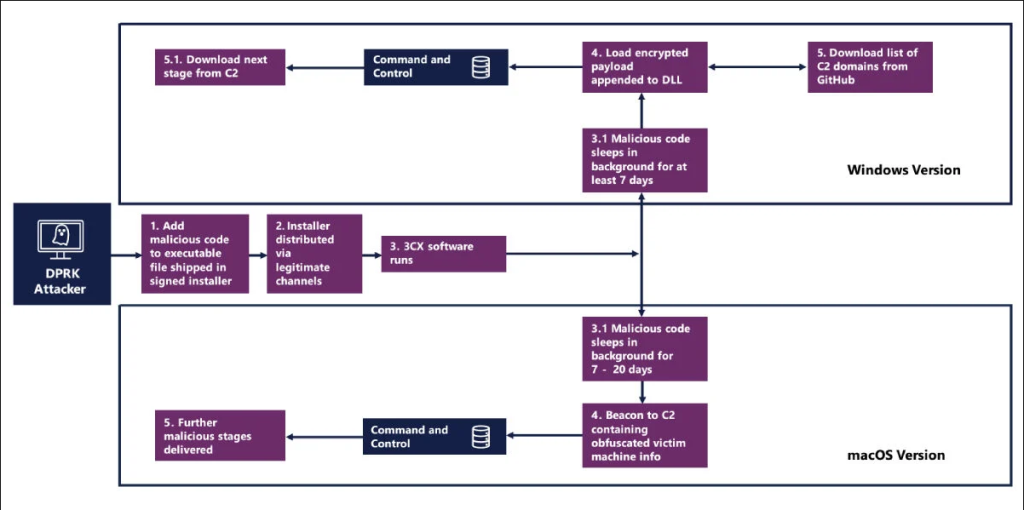
Diagram of the 3CX attack chains on Windows and macOS, courtesy of the NCSC and NIS
The current warning comes a day after Microsoft published its own report on another North Korean supply chain attack on CyberLink’s multimedia software. Lazarus breached the Taiwanese tech company and tampered with its installer as recently as October 20. Microsoft said that the malicious installer has been executed on over 100 devices across various territories, including the US, Canada, Japan, and Taiwan.
The software scans the victim’s system for evidence of CrowdStrike Falcon, FireEye, or Tanium EDR security solutions. If they are found, malicious activity stops, and the software runs normally. If the victim isn’t running any of the three security products, then the software attempts to download the second-stage payload embedded within a fake header of a PNG file, launching it in memory. That payload then attempts to contact two URLs, both of which are illegitimate but have been previously compromised by the group.
Microsoft made indicators of compromise (IoCs) available to help defenders detect Diamond Sleet activity on their network.

